
In a bypass attack, the attacker’s main aim is to get information and put a file or code into the targeted system. This code can be harmful and can come in different types, like PHP, ISP, or JS files. Once the attacker puts this code in, they can easily connect to the server from somewhere else using a web shell GUI. Bypass attacks are pretty common in website security. For instance, attackers might use techniques like SQL injection or application exploits (like command injection, SQL injection, and brute force attacks), or they might use bots.
Challenges in Identifying Bot Activity:
Imagine a situation where a website seems normal, but suddenly, there’s a weird increase or decrease in visitors. It’s hard to tell if these visitors are real people or automated bots. Also, in cyber attacks, there are other strategies like social engineering, reverse engineering, and SYN flood attacks, which are often used in Distributed Denial of Service (DDoS) attacks. SYN flood attacks involve sending a huge number of SYN/ACK (Synchronize/Acknowledge) requests to overwhelm the system and make it impossible for real users to access it.
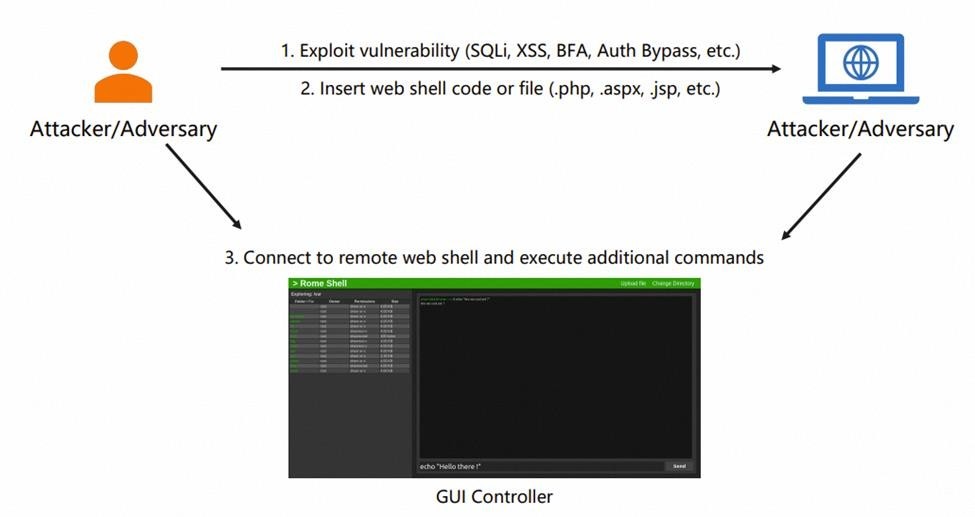
Image Source: Alibaba Cloud
How WAF works
Setting up a Web Application Firewall (WAF) is really important to stop all kinds of attacks. The WAF sits at Layer 7 of the application stack and keeps an eye on HTTP/HTTPS traffic between your application and the internet. You can use this flexible security system in different places, like in the cloud, with different cloud providers, or on your own servers.
Here’s how it works: normally, when someone wants to visit your website, they type in the domain name. A DNS server then finds the IP address linked to that domain and sends the visitor to the right server. But with a WAF, things are a bit different. Users first talk to the DNS to get the website’s DNS name because WAFs work like a redirect system. Instead of showing the real IP address, the DNS gives out the WAF’s name. This means attackers can’t see the actual IP address, which makes things more secure. Every request from users goes through the WAF before reaching the server. This means the server’s IP address stays hidden from the public eye right from the start.
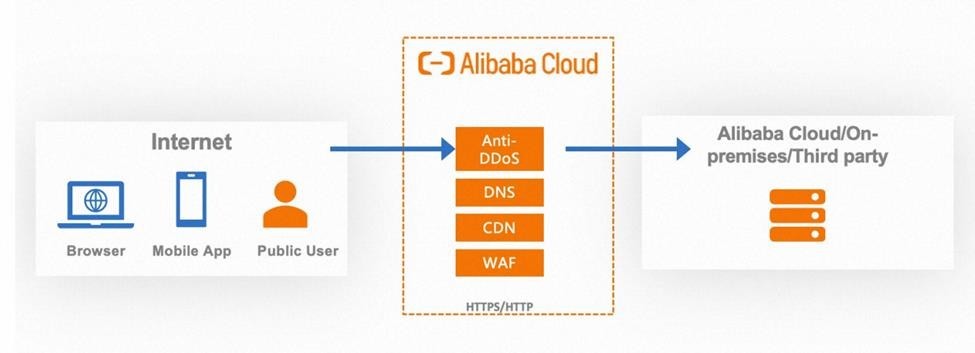
Image Source: Alibaba Cloud
Case 1: SQL Injection
In this use case, a user inputs a query to locate the city of Tokyo. However, the attacker exploits a vulnerability by injecting a semicolon command into the SQL query and attempting to execute other susceptible queries. When security measures are low, the system becomes vulnerable to the deception caused by the semicolon command. Consequently, the attacker can easily blend query, leading to data loss in the Tokyo table.
Case 2: Scripting Vulnerabilities
When a website’s security is weak, anyone, including potential attackers, can exploit it. They can mess with the website’s code by adding their own scripts. These scripts might redirect users to shady content like gambling or adult sites, making visitors wonder if the site’s been hacked or if it’s supposed to be showing this stuff.
Scenarios:
Web Application Firewalls (WAFs) are super important in places like ticketing websites. Here, lots of bots or web crawlers might try to book tickets without actually buying them, leaving real customers with no tickets. This hurts both the customers and the company’s profits.
The need for WAFs also pops up in e-commerce and real estate websites, where lots of people visit. Weak spots in the website’s code can lead to scams. For example, scammers might change the contact info of sellers, making it easy for them to trick people. These examples show how vital WAFs are in keeping different industries safe from all sorts of threats.
WAF Capabilities:
Web Application Firewalls (WAFs) are powerful tools that can:
- Tackle common online attacks, protecting against ten common types identified by OWASP.
- Help against big attacks like DDoS, which try to overwhelm websites with too much traffic.
- Block harmful IP addresses and regions that cause trouble.
- Keep an eye on website traffic and come with preset rules to help manage it.
- Control which ports on your servers are open for communication.
- Manage lists of safe and unsafe IP addresses, letting you decide who gets access.
- Protect any part of your website, even specific subdomains, to make sure everything stays safe and secure.
Content Delivery Network ( CDN)
When it comes to speed, the WAF system keeps your website safe without slowing things down when people visit. But, to make things even faster and take some pressure off your server, you can use Content Delivery Networks (CDNs). CDNs store popular website content so users can get it super quickly from nearby servers instead of waiting for it to come from the main server. This speeds things up a lot and still keeps your website secure with the WAF. When a server already has a request stored, new users asking for the same thing can get it right away from the cache. But if the request isn’t saved, it has to go to the main server to get it. CDNs are set up to save requests, so your website doesn’t have to rely on the main server all the time. This is especially handy if your main server is far away, as CDNs cut down on the time it takes to get stuff because they store it closer to users.
WAF and Anti-DDoS
WAF can stop some DDOS attacks, but for extra protection against them, it’s smart to add more Anti-DDoS measures. DDOS attacks can happen at different levels: Layer 4, which deals with network stuff like TCP and UDP, or Layer 7, which handles things like web browsing (HTTP and HTTPS). In an Elastic Compute Service (ECS) setup, you can use the security group feature to block traffic on certain ports like 80 or 443 to stop Layer 4 attacks. If an attack hits at Layer 7, the WAF can help out, but adding extra Anti-DDoS measures is still a good idea for better protection. When you’re not sure how big the attack is, it’s wise to start with the WAF because keeping an eye on incoming requests is key. If the number of requests suddenly skyrockets, like going over 100,000 per second, adding Anti-DDoS measures can give you even more security.
Conclusion
In wrapping up, make sure your web applications stay safe, keep your data protected, and boost your cybersecurity with the top-notch security solutions from Alibaba Cloud WAF. Partner with us, YVOLV, as we work together to create a safer and stronger online environment in the Mena Region.
